Approach to the cybersecurity of critical infrastructure with particular attention to port infrastructure.
Diego Fasano
CYBER RISK IN THE PORT AREA
Port facilities need to adopt adequate measures to protect not only against physical security threats but also in terms of cyber security. Cyber attacks on computer systems aim to steal valuable data and compromise the supply chain, with damaging consequences for port and maritime systems. Since the release of the first study on cyber security in the maritime sector titled Analysis of Cyber Security Aspects in the Maritime Sector, regulations and risks for information handled and stored on computer systems, operational processes, and systems related to Industry 4.0 have significantly evolved. The digital transformation opens up the company’s production and operational processes to the Internet, which is necessary to enable the full functionality of new technologies.
There is a regulatory and general best practice framework, but it needs to be inserted into a process structure that is suitable for minimizing business risks and preserving operational continuity in the event of a cyber-attack or system malfunction. An essential initial phase of risk assessment is risk identification, a process of identification, recognition, and description of the risk, based on the following activities: identification of assets to be protected (information and media that contain them), identification of possible threats, the definition of implemented protective measures, and then reduction of identified risks.
CRITICAL ASSETS
Identifying and describing in detail the relevant assets in the port context provides an important contribution both to the risk assessment activities conducted on the safety of data and information (with particular reference to the technical standard ISO/IEC 27001) and within the ambit of the risk analysis foreseen by the port security regulations and relating to the formation of the Port Facility Security Assessment (PFSA). A recent study isolates ten macro-categories of typical informative and processing assets in the port-maritime sector. Below are the most relevant ones:
Information: the information and declarations that ships must communicate to the competent authorities before entering port, according to international, community, and national regulatory provisions. In addition to these, there is the necessary information to organize and manage services for the ships, so-called “operational data”, shared navigation data with the port, commercial information regarding reservation of mooring services, and related traffic data. Personal data processed in relationships between the port and shipping companies and maritime navigation must also be considered among the informational assets. In relation to cruise traffic, personal data communicated directly by passengers for the provision of specific services may be of relevance.
- Information: the information and declarations that ships must communicate to the competent authorities before entering port, according to international, community, and national regulatory provisions. In addition to these, there is the necessary information to organize and manage services for the ships, so-called “operational data”, shared navigation data with the port, commercial information regarding reservation of mooring services, and related traffic data. Personal data processed in relationships between the port and shipping companies and maritime navigation must also be considered among the informational assets. In relation to cruise traffic, personal data.
- Information and data management: data processing assets are the broadest macro category and include IT and OT systems and networks with related end-user devices for professional users, communication networks, and related components.
- People: employees of port authorities, port facilities, and moored ships, as well as authorized members of the public and passengers who have access to the port area, use its systems, and handle its data.
THREATS TO INFORMATION SECURITY
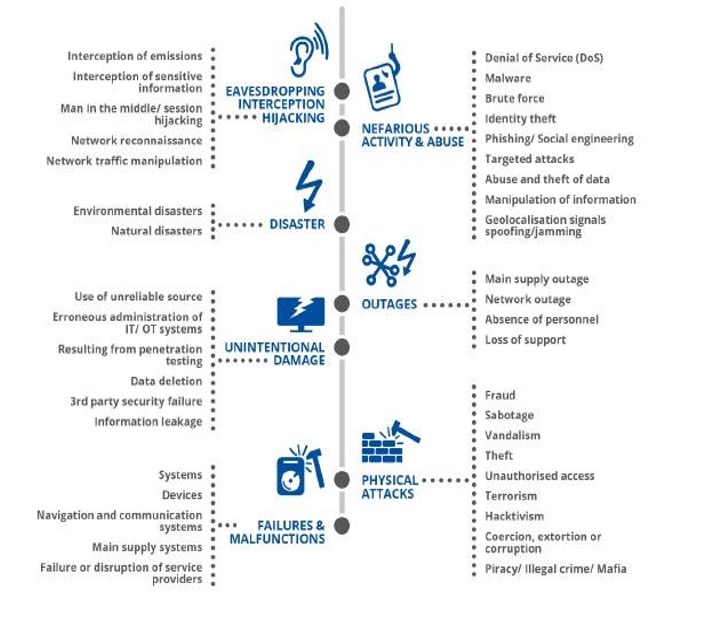
Recent studies propose a list of possible scenarios of cyber threats impacting the security of data and information in the port ecosystem. The identified risks, except for physical attacks and natural disasters, regard the assets of information and data processing and threats techniques with abuses and malicious behaviors, such as DoS attacks, malware usage, brute force attacks, identity thefts, social engineering, targeted attacks, data manipulation, unauthorized modifications of GPS signals of ships and navigation routes.
In addition to these threats, there are interception techniques for communication between ports and ships, sensitive data interception, and man-in-the-middle attacks, in which someone secretly retransmits or alters the communication between two parties who believe they are communicating directly with each other.
Some structural vulnerabilities of the port system facilitate the success of various types of attacks. The first shortcomings identified by recent studies concern the lack of basic digital culture in the port ecosystem, even before the lack of culture and training in security and cybersecurity. The budgets allocated for investments related to cybersecurity are therefore limited, and there is a lack of qualified personnel capable of coordinating, developing, and maintaining IT and OT (Operational Technology) projects. It is necessary to maintain a necessary updating on the themes of innovation and emerging threat techniques, also related to the development of specific projects for the digitalization of production processes in ports, through the use of tools typical of Industry 4.0.
There is then a structural gap in regulations regarding cybersecurity. The European NIS Directive and its implementing legislative decree pave the way and legitimize the role of cybersecurity for information, but there are still no suitable ad hoc measures to impose the adaptation of the port ecosystem to adequate levels of cyber security (with an allocation of the relative budget). However, cyber threats towards the sector continue to grow and the role of ports and port facilities is essential as critical infrastructures at the national level. They can be identified as operators of essential services, a relevant qualification in relation to their possible inclusion in the national cyber security perimeter, according to Law No. 133/2019.
PORT ASSETS OVERVIEW
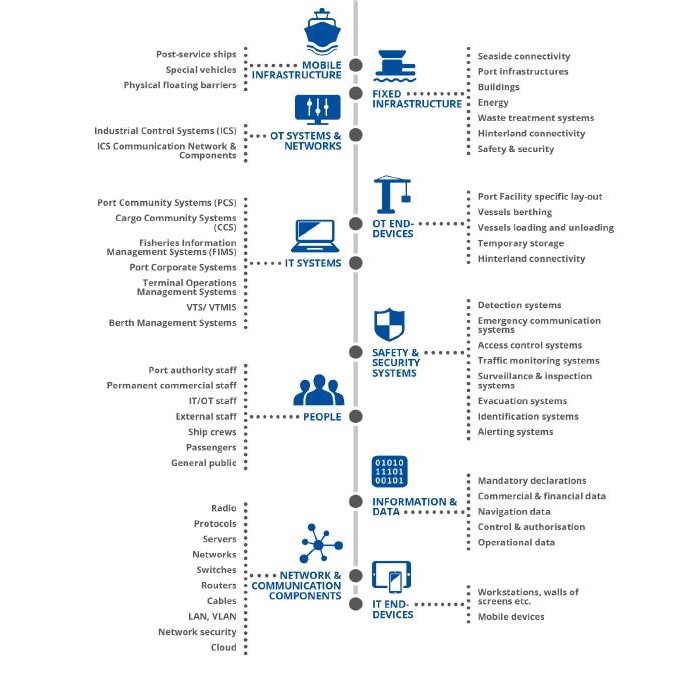
To identify cyber threats associated with the port ecosystem, it is essential to start with the identification and decomposition of port assets. Figure 1 provides an overview of the main categories of assets that can be found in a port and details the assets for each category. This taxonomy should not be considered complete; it aims to represent the main resources and does not reflect the diversity and specificities of different ports.
Based on various sector research, ten categories of assets have been identified: fixed infrastructure, mobile infrastructure, OT systems and networks, associated OT end devices, IT systems, IT endpoints – associated devices, communication networks, and components, security and protection systems, information and data, and people.
THREATS AND CHALLENGES OF CYBER SECURITY IN PORT ECOSYSTEMS
Ports face numerous cybersecurity challenges, some of which are fairly generic in any IT and OT environment, while others are quite specific to port ecosystems. Table 1 identifies the potential impact of cybersecurity incidents on a port.
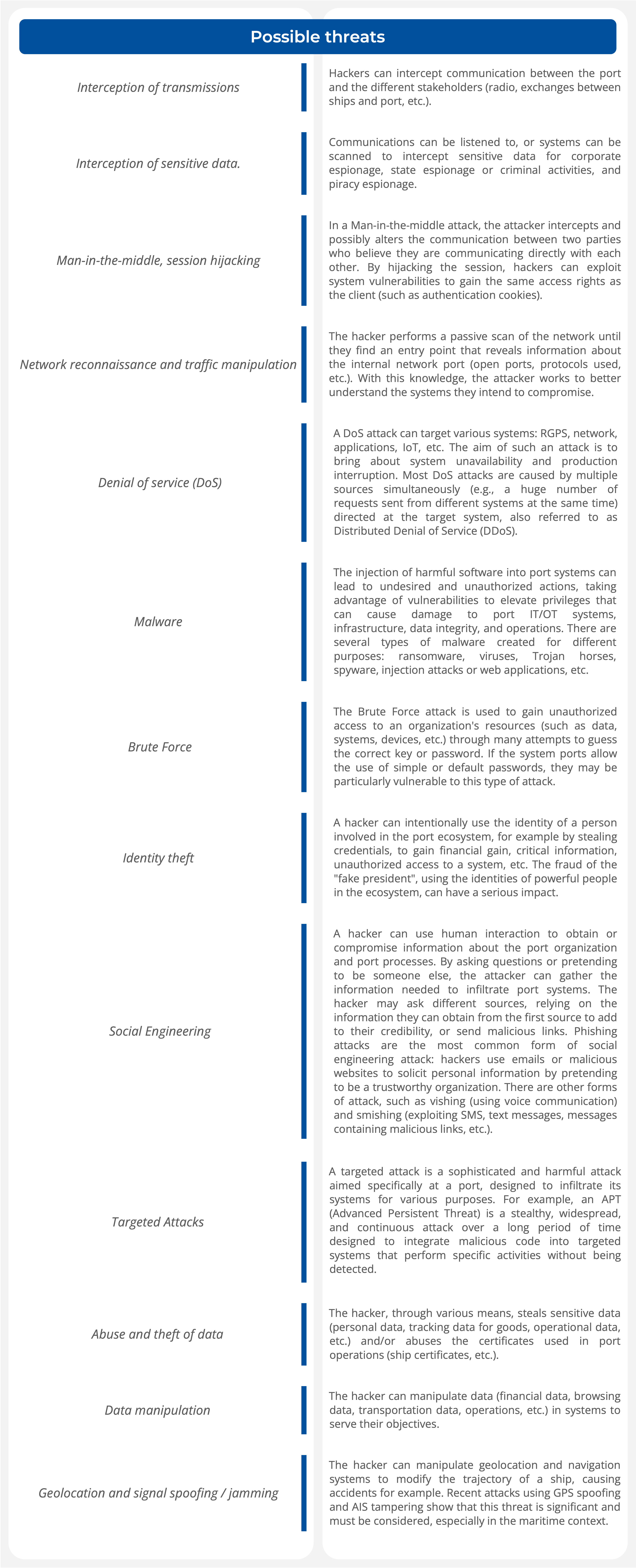
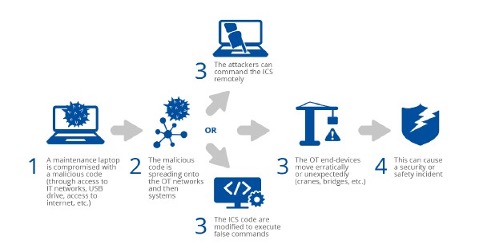
SCENARIO OF A TYPICAL CYBER ATTACK
Scenario A – Compromise of critical data to steal high-value goods or enable illegal traffic through a targeted attack
This scenario is a sophisticated and targeted attack on port systems (Advanced Persistent Threat): the attackers must have in-depth knowledge of port systems and networks (social engineering, network scanning), port processes, and port infrastructure (physical intrusion) to carry out goods and container theft. An example of such an attack occurred in one of the port terminals in Antwerp, Belgium, where a drug cartel took control of container movements and retrieved the necessary data to collect them before the legitimate owner.
On one hand, attackers identify and retrieve authentication data (credentials) to access useful systems:
- The attackers gather information about the port systems through social engineering. They then identify the targeted systems used for handling goods and containers, as well as the identities of the people who use them.
- Once identified the systems and their operators/users, attackers launch phishing attacks to retrieve login credentials for such systems.
- On the other hand, attackers install components to remotely access the Port Network and bypass network security.
- The attackers scan the network ports to find vulnerabilities to exploit and gather information or install components for remote access to the network ports (wireless access point) if necessary, through physical intrusions.
- To guarantee constant access and adaptation to any network and infrastructure changes in the long term, networks are monitored.
- The attackers now have access to cargo tracking systems and other objects boasting port systems and can access critical information about the containers they want to steal (location, content, pick-up code, etc.) from outside the port facilities.
- The attackers can then steal the load before the official pickup date.
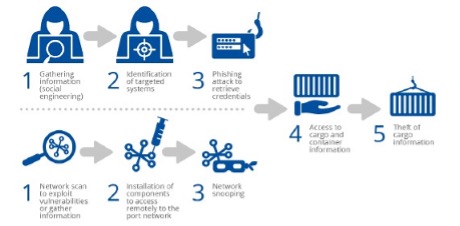
Scenario B – Ransomware propagation leading to a total shutdown of port operations
This scenario can be a targeted or untargeted attack (as collateral damage of a targeted attack on other companies through the propagation of ransomware): hackers can develop ransomware exploiting different vulnerabilities to spread it in the network ports and encrypt different systems and devices (workstations, servers, etc.), leading to the destruction of infected systems and potential loss of backups (inside servers that could be encrypted). An example of a malware attack similar to ransomware was the widespread incident that affected Maersk’s operations. In this case, it was a destructive malware and widespread ransomware attack (NotPetya) that hit Maersk. This attack led to the total paralysis of Maersk’s Rotterdam terminal, with high risks of security and safety incidents, and manual management of port terminal operations for over two weeks.
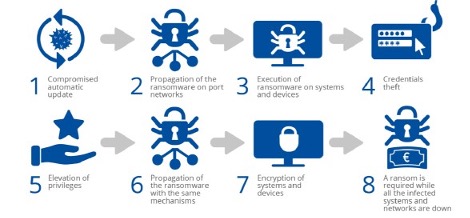
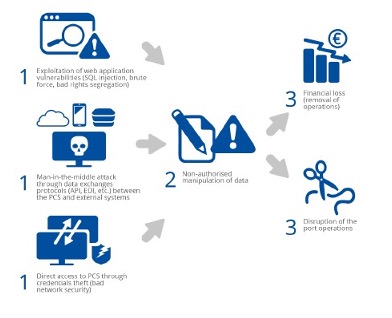
Scenario C – Compromise of the port community system for data manipulation or theft
This scenario is a targeted attack on the systems used for exchanges between all stakeholders, usually the Port Community Systems. The objectives are to falsify information about port services in order to disrupt operations or modify certain processes in the systems (resulting in financial loss for the port). This scenario is realistic because these systems are exposed to all interested parties in different ways (usually using different networks and systems, machines). In fact, these systems are increasingly automatically interconnected with external systems (through APIs, EDI exchanges, etc.): Third-party systems thus become an additional surface of attack to reach port systems. Since these systems vary from port to port, there may be different ways to set up this attack: for example, if Port Community Systems are exposed through a web application, the attacker can exploit common vulnerabilities in web applications; if it is an application developed internally by developers employed by the port and if standard security development rules are not applied, specific vulnerabilities can be exploited; and so on.
Scenario D – Compromise of OT systems that causes a serious incident in port areas
This scenario is specific to the OT world and ICS specificities and is considered realistic even though such attacks on ports are not publicly known. In fact, similar attacks occur in other critical sectors, especially in the energy sector. This type of attack does not need to be generally sophisticated to have an impact, but the greater risks remain in the connection with external networks and systems, particularly the Internet. The specificities of such attacks are the close link between the physical and logical worlds: the attack usually starts in the logical world (from the IT component) and has impacts in the physical world (damage to OT systems and end devices, incident security and protection, etc.). A port contains various OT networks, systems, and end devices used for different services and operations and owned, managed, and maintained by different stakeholders: cranes for loading and unloading ships at port terminals, bridges at the port entrance to let ships in and out, systems in refrigerated warehouses to keep delicate foods at a safe temperature, sensors, and systems used for transportation, storage, and monitoring of hazardous goods, etc.